Cybersecurity threats are on the rise, small and medium sized businesses are more vulnerable than ever before. Vulnerability Analysis is needed in today’s business to help protect valuable data. CMMC assessments assist government contractors in securing controlled unclassified information (CUI) in their organizations.
Table of Contents
Defining a Maturity Model
Maturity models are modeling tools used by both technical and non-technical managers of an organization. When determining a typical Cybersecurity Maturity Model (CMMC), the following attributes are used:
• Inadequate Information Security Measures or Software Defined (SD) Access Management: A red flag indicating that the organization has made strides but still has room to improve.
• Weakest Point: They have created a security posture that is full of weaknesses and susceptible to attack.
• Best-in-Class: This maturity model is one where the organization is already seen as a best-in-class in terms of its security measures, security vulnerabilities and mitigation of risk.
• Global Scope: The maturity model covers the organization globally.
What is Cybersecurity Maturity Model Certification?
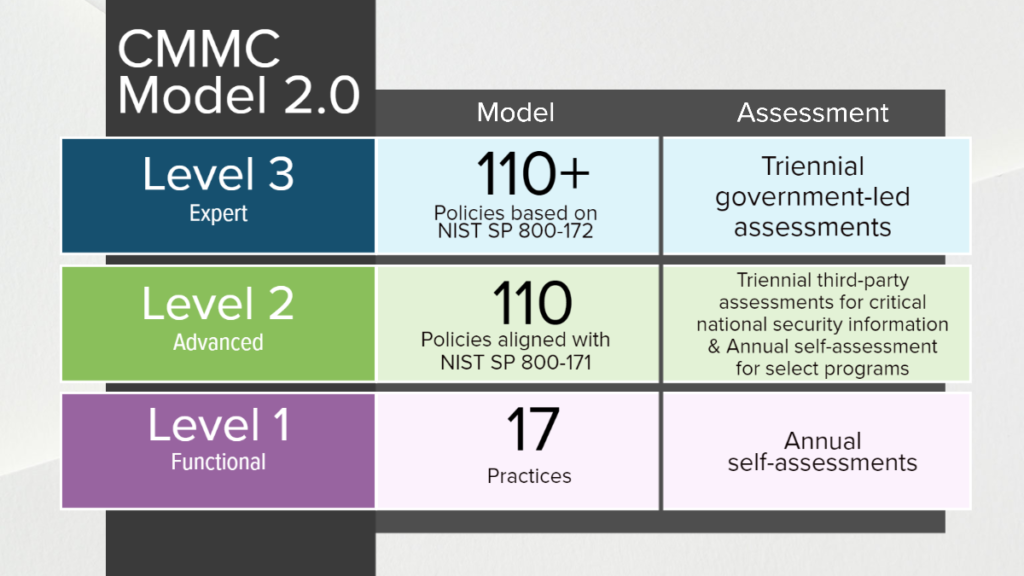
Cybersecurity Maturity Model Certification (CMMC) is a certification program developed by ISACA for security professionals. CMMC assesses an organization’s readiness to protect itself from cyber threats. Each assessment is based on a scenario or a series of possible scenarios. The scenarios are grouped into different maturity levels which are identified by the IT services that are currently in place.
What’s the Process Like?
First, you will receive an assessment questionnaire. Once your answers are verified, you will be asked to participate in a specific scenario, similar to security awareness training.
CMMC certifications range from Certified Information Systems Security Professional (CISSP) to Certified Information Security Manager (CISM) and Certified Information Systems Security Engineer (CISE).
What Should I Know Before Going through the Certification Process?
Cybersecurity Maturity Model Certification is designed for people who work with highly sensitive unclassified or private data. This usually includes cybersecurity professionals, business executives and information security managers. Knowing the methodology and identifying your weaknesses will assist in addressing areas in need of improvement.
Why Get Certified?
Most Information Technology professionals are familiar with Cybersecurity maturity models. CMMC demonstrates a commitment to building stronger partnerships in the IT Community. Because CMMC is automated and continuously improves, it can be quickly implemented in new organizations.
CMMC is a valuable resource for organizations. It presents a clear and concise list of roles, responsibilities, and metrics. It provides a list of actions required for the organization to implement appropriate security controls. CMMC is helpful for improving organizations’ cybersecurity capabilities and is accepted as an industry best practice.
How to Get Started with CMMC Certification
Cybersecurity Maturity Model Certification is a federally mandated program which sets requirements for organizations to continually review and adapt to changing cybersecurity threats. The CMMC program and certification best practices have been developed to ensure that organizations meet the minimum standards to qualify for federal CMMC program funding. CMMC certification is required for all federal contractors, including small businesses, who may not otherwise be able to meet CMMC’s requirements, including security clearance, risk management, incident response, security awareness, and training. If your organization does not qualify for a competitive CMMC for your role or business, then it is best to acquire a Public Sector Certification from the government.
Cost and Time
CMMC certification requires an initial assessment and is not a burden to anyone. CMMC assessment is a one-time fee and provides up to 60 hours of online education. CMMC certification takes place in an online learning environment and is helpful in businesses that have a real-time, virtual connection to the Internet.
Technical Requirements
Applicants must complete two validated assessments and submit documents supporting individual findings to verify their CMMC. Applicants must be trained and certified on both the Open Web Application Security Project (OWASP), Common Vulnerabilities and Exposures (CVE) and the Common Weakness Enumeration (CWE). They must be prepared to provide documentation to support their findings. Applicants will perform both assessment projects using MIT’s Python, SQL and a Web Application Framework using Amazon Web Services, Platform.js or nginx. The Python software framework will be used to analyze the code. The SQL will be tested to see if security issues were identified.
Non-Technical Requirements
- Experience as an advanced security professional Experience in CMMC assessments
- Valid driver’s license or state-issued ID
- Previous security or related experience in a company with strict/confidential/security policies
- Extensive knowledge of classified CUI Experience with Java or J2EE.
Conclusion
The information security industry is rapidly evolving and being disrupted by new technologies and threats. One of the most fundamental threats to a growing business is security awareness and training. You must stay informed on security industry trends and improvements. A better understanding of the latest developments and security issues is essential to better your organization’s security posture and protect customer data. By following a CMMC certification training program, you can become a certified security analyst that will help your organization protect its digital assets. The Cybersecurity Maturity Model Certification and Vulnerability Analysis training is offered on-site at the in-house cyber range.
Learn more
OUSD Acquisition & Sustainment – SECURING THE DEFENSE INDUSTRIAL BASE CMMC 2.0